Get Complete Visibility on the Flow of Consent-Based Financial Data
Track API interactions, consent flows, and data sharing across banks and financial institutions. Ensure secure, compliant operations while maintaining user trust at scale.

Powers 28 Billion+ Monthly Transactions for Industry Leaders
























The Consent-Driven Data Sharing Challenge
API Complexity Across Institutions
When data retrieval fails, identifying whether it's your system, a Financial Information Provider (FIP), or a Financial Information User (FIU) integration becomes difficult.
Scale Without Compromising Security
Traditional monitoring can't differentiate between performance issues and potential incidents in real-time.
Compliance Is Non-Negotiable
Manual tracking makes it impossible to prove compliance during regulatory audits or detect unauthorized access patterns before they escalate.
Error Handling Across the Ecosystem
Without clear visibility into error sources and business impact, support teams struggle to provide timely resolutions.
Complete Observability of the AA Ecosystem

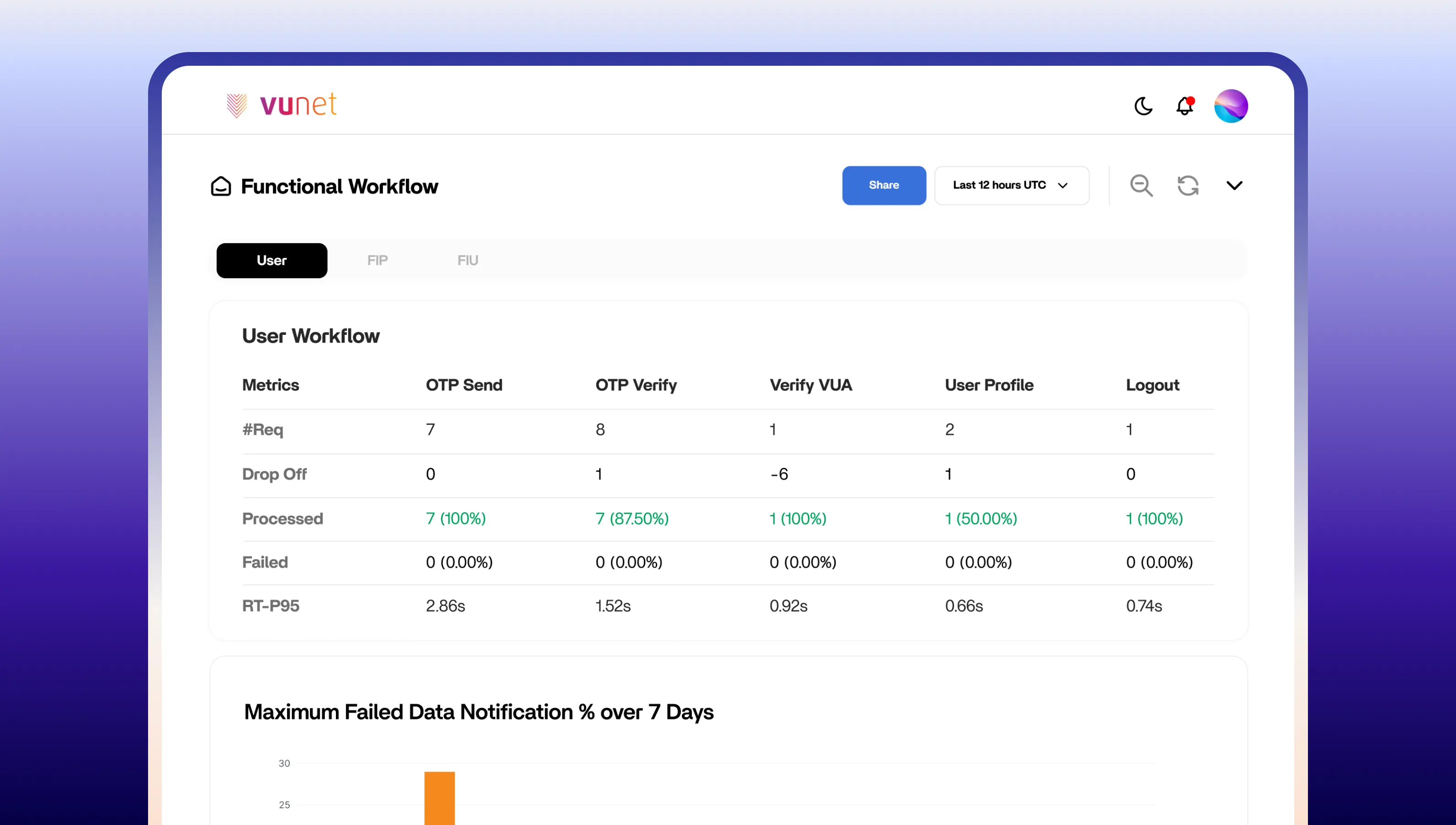
API Interaction Monitoring
- Track API success rates, response times, and data retrieval timelines across all Financial Information Providers (FIPs) and Financial Information Users (FIUs).
- Monitor consent requests, failures, and successful responses with performance metrics at the integration points.
- Identify bottlenecks in API interactions and optimize performance to enhance user experience.

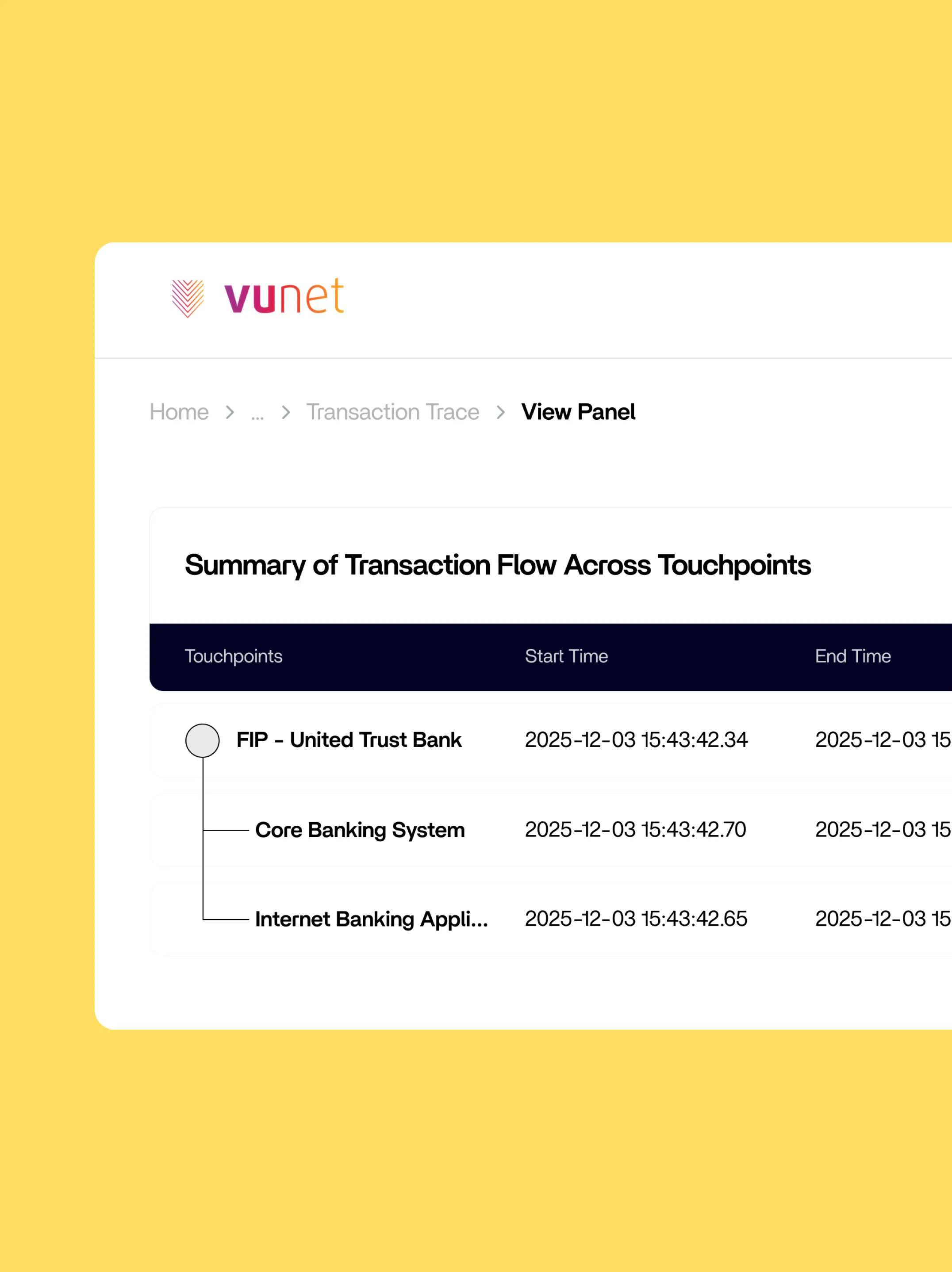
Journey-Level Visibility With Transaction Tracing
- Follow each consent journey from request through approval to data sharing using transaction-level unique identifiers for complete traceability.
- Track data flow across multiple API service touchpoints with unified visibility across previously siloed systems.
- Enable dispute resolution and audit support with comprehensive transaction histories and exact failure point identification.

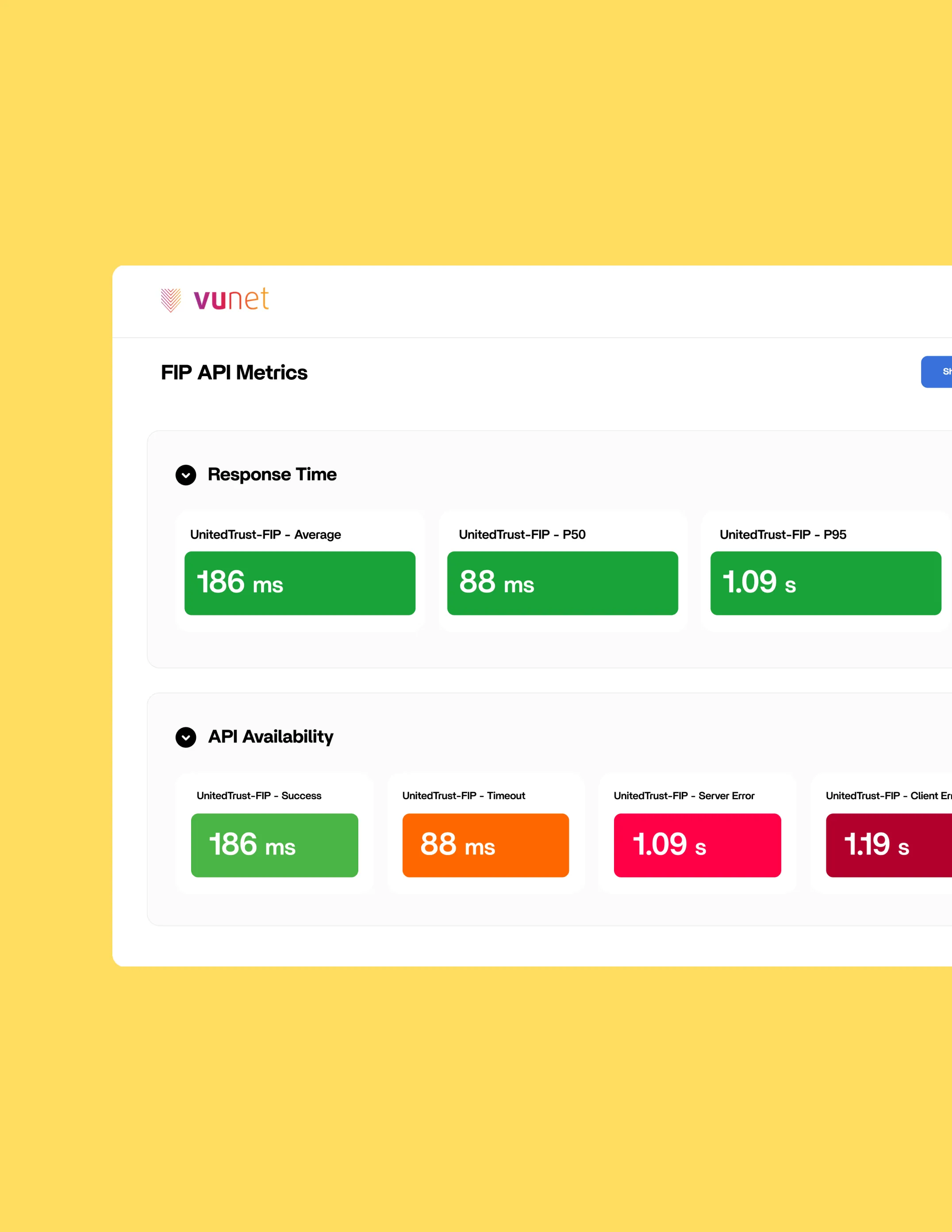
Security and Compliance Monitoring
- Monitor request patterns and detect any anomalous request patterns or violations.
- Track audit trails automatically for every data access request, consent modification, and user interaction.
- Maintain RBI-mandated data protection standards with automated compliance reporting.


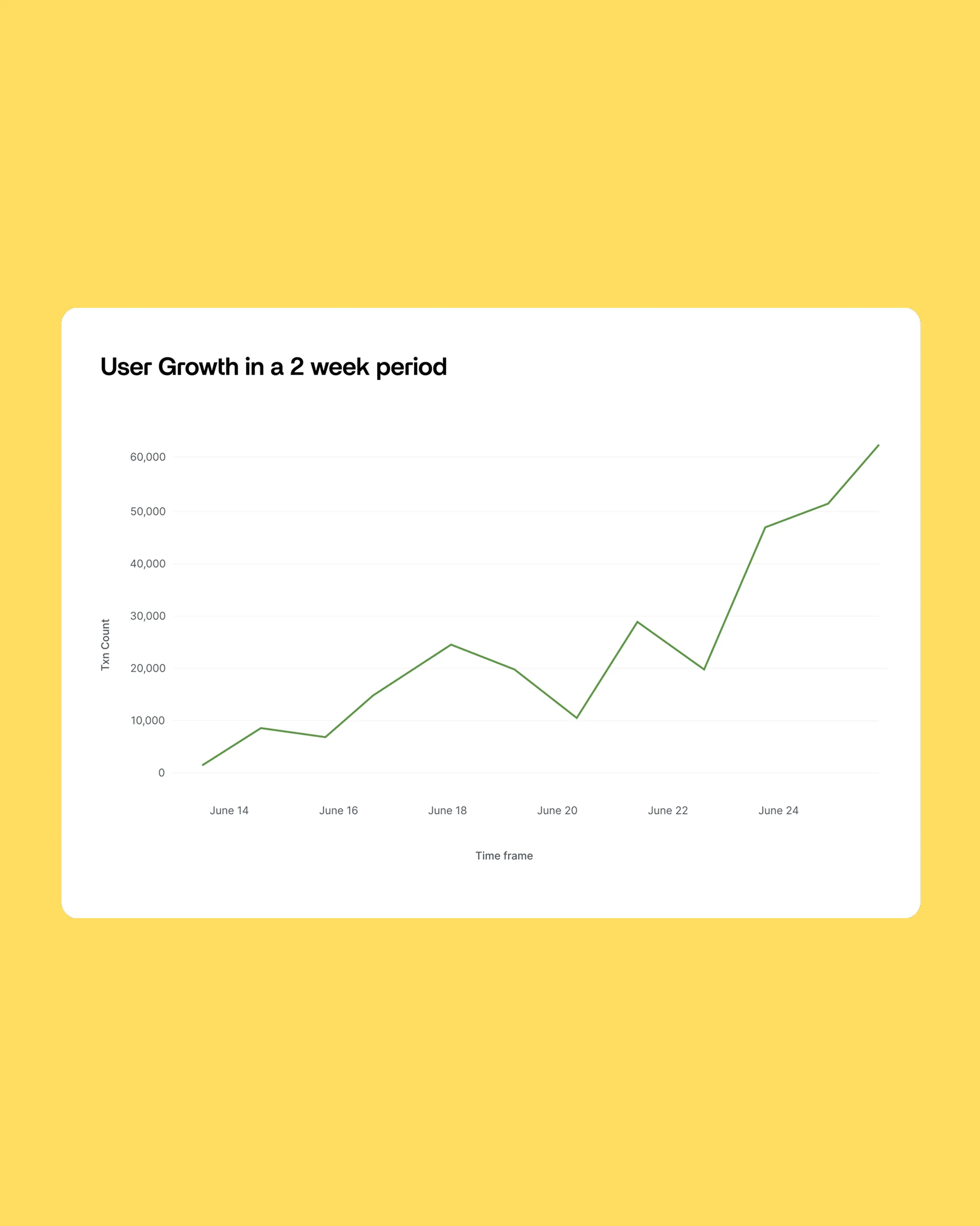
Dynamic Scaling and Performance Optimization
- Monitor user growth patterns and transaction volumes to identify when resources need scaling.
- Track performance trends across time periods, user segments, and institution types to optimize infrastructure allocation.
- Ensure cost efficiency by scaling resources dynamically based on actual demand patterns rather than static estimates.

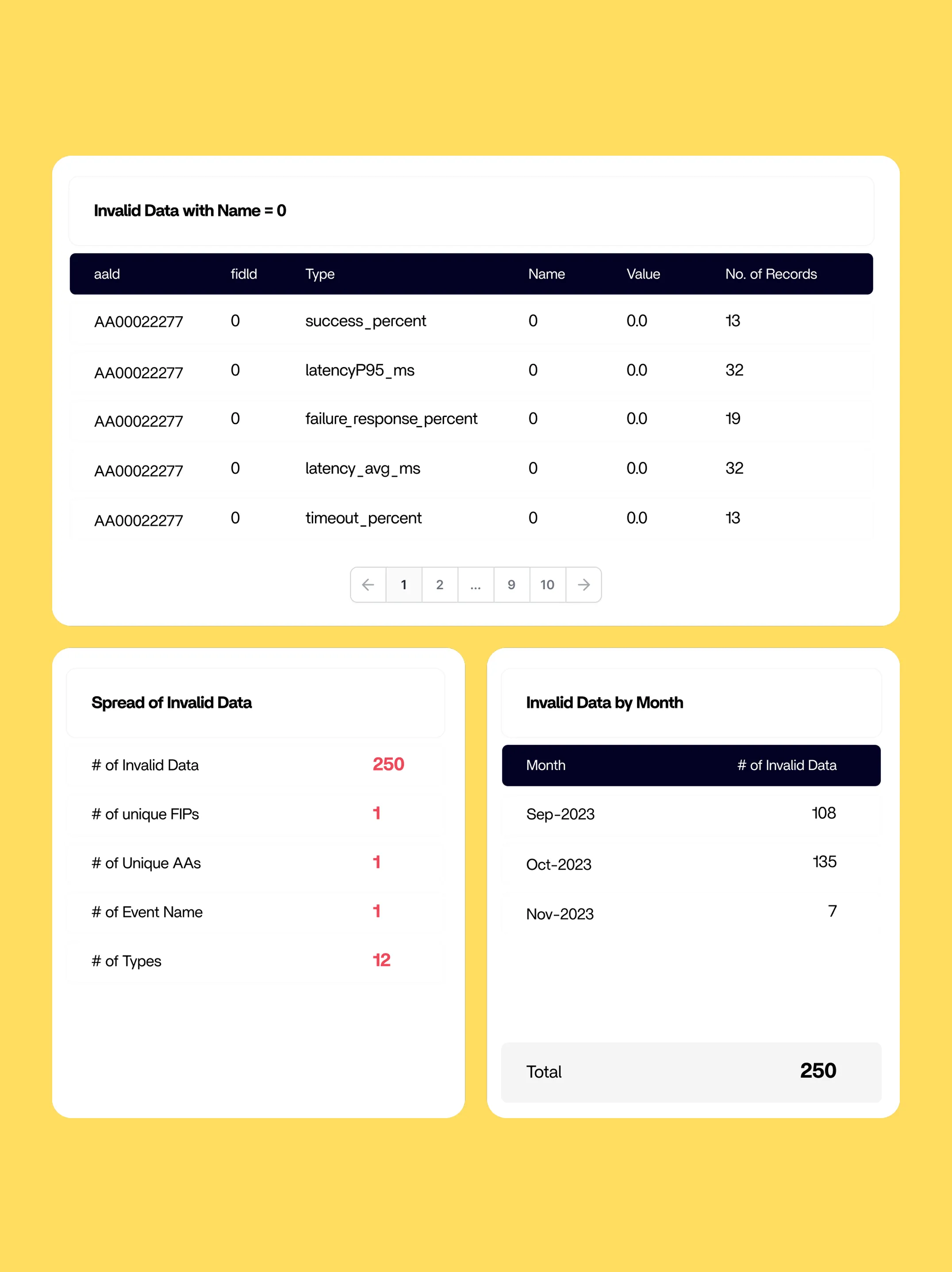
Intelligent Error Handling and Alerting
- Monitor error rates across the ecosystem with alerts prioritized by business impact rather than just technical severity.
- Receive contextual notifications via dashboard, WhatsApp, email, SMS for consent flow failures, FIP/FIU integration issues, data retrieval timeouts, compliance violations, and security anomalies.
- Improve incident response times with operational dashboards providing real-time visibility and root cause analysis.

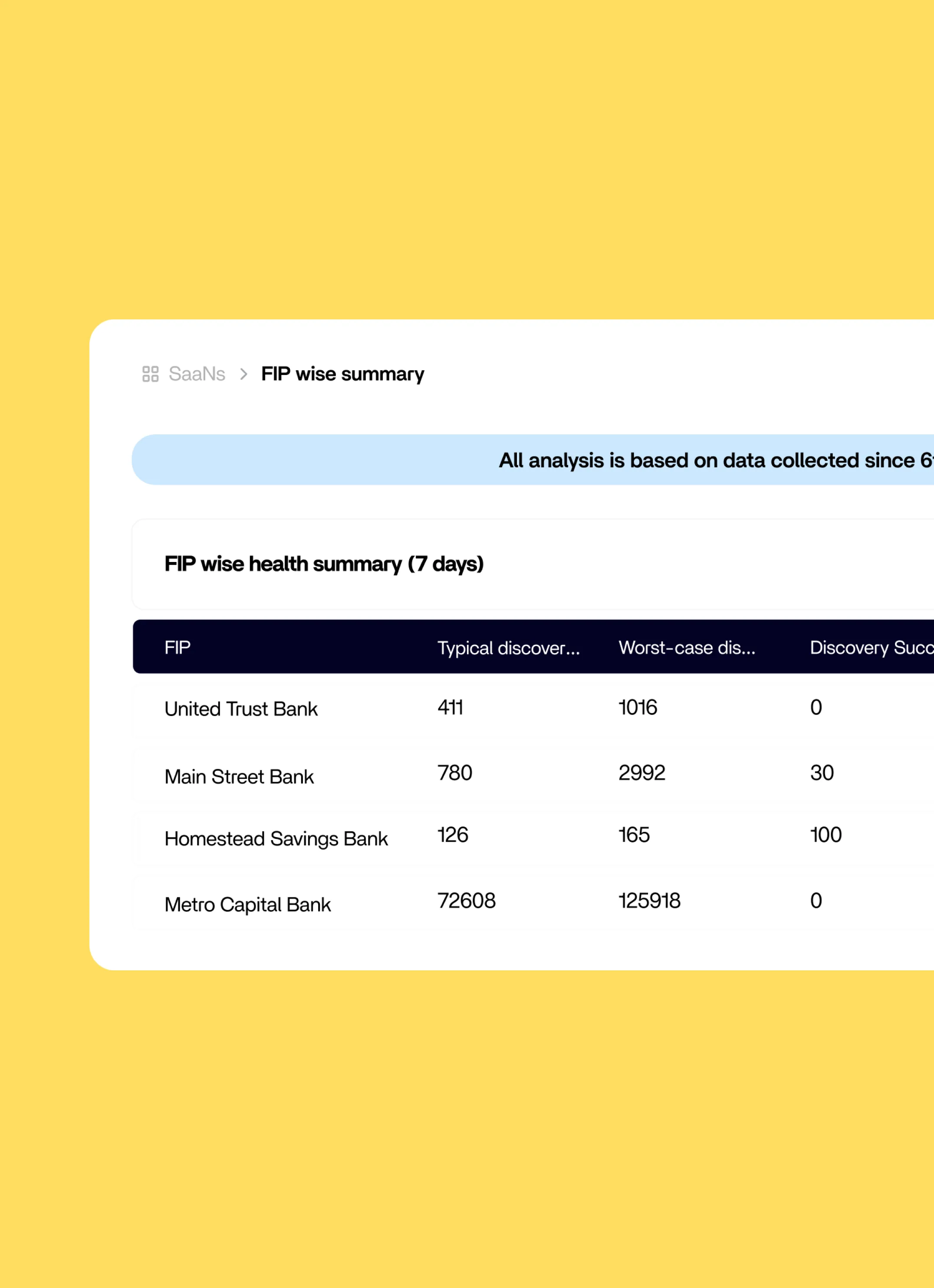
Aggregated Ecosystem Analytics
- Collect performance statistics across all institutions, consent types, and data categories to identify trends and optimization opportunities.
- Generate ecosystem governance insights showing which FIPs/FIUs perform best, common failure patterns, and user experience metrics.
- Access operational dashboards combining technical performance with business outcomes for data-driven decision making.
Business Observability That Delivers Bottom-Line Results
Built For Secured Consent-Driven Data Ecosystems
Multi-Institution Visibility
Monitor your AA platform alongside all connected FIPs, FIUs, and third-party integrations from a unified platform without fragmented tools.

Compliance-First Design
Automatic audit trail generation, encryption monitoring, data access tracking, and regulatory reporting capabilities built for financial services requirements.

Frictionless Integration
300+ adaptors connect to AA platforms, banking APIs, consent management systems, and security infrastructure without code modifications.